PRIVACY IMPACT ASSESSMENT TEMPLATE PROJECTS OR ACTIVITIES THAT INVOLVE
HEART OF LIFE SPIRITUALITY CENTRE PRIVACYINFORMATION PRIVACY INDIVIDUAL ACTION PLAN HONG KONG CHINA
PRIMARY SCHOOL PRIVACY NOTICE PLEASE READ THIS NOTICE
!doctype Html html Langenus head meta Charsetutf8script Typetextjavascript(windownreum||(nreum{}))init{privacy{cookiesenabledtrue}ajax{denylist[bamnrdatanet]}distributedtracing{enabledtrue}}(windownreum||(nreum{}))loaderconfig{}! for
050 PRIVACYREGLEMENT PERSONEELSGEGEVENS SOORT DOCUMENT REGELING INGANGSDATUM 01012011 LAATST
0S PRIVACY SECURITY HIPAA PRIVACY RIGHTS AND OPERATIONS GUIDE
Personal Profile Development
Privacy Impact Assessment Template
Projects or activities that involve processing or sharing personal data/information or commercially sensitive data/information give rise to privacy issues and concerns. To enable an organisation to address the privacy concerns a privacy impact assessment (PIA) can be used to assess privacy risks to individuals in the collection, use, storage, disclosure and disposal of data/information. The PIA can help identify privacy risks, foresee problems and bring forward solutions.
For Use With (not exhaustive):
New projects
Changes to existing projects/procedures/systems
A data sharing initiative where two or more organisations seek to pool or link sets of personal data
A proposal to identify people in a particular group or demographic and initiate a course of action
Using existing data for a new and unexpected or more intrusive purpose.
Information Sharing Protocols
Relocation of staff or equipment
Stakeholder Engagement e.g. surveys
Please complete this document in conjunction with the Privacy Impact Assessment Guidance Document. There is also a checklist within the guidance which will assist you with deciding whether you need to complete a PIA.
|
For IG Team use only |
|
|
Date received: |
|
|
Received from: |
|
|
PIA tracking number: |
|
|
Date of PIA panel: |
|
|
Date reviewed: |
|
|
Date feedback given: |
|
|
Background Information |
||||
|
Project/Activity Name: |
Eclipse Live / VISTA |
Date of PIA submission: |
Nov 18 |
|
|
Project/Activity Leads Name: |
|
Project/Activity Leads Contact Details: |
|
|
|
Sponsor (e.g. Project Board): |
|
Lead Organisation: |
|
|
|
Name of individual submitting this PIA/Key contact:
|
||||
|
What is the purpose of the PIA?
To identify the risks to the rights and freedoms of data subjects, posed by the existing system and proposed changed and to identify where privacy by design can mitigate those risks.
|
||||
|
Brief description of proposed overall activity and activity period:
Eclipse Live currently provides extraction and aggregation of primary care data to support case finding for the practices and risk stratification for the CCG.
This will now be altered to add the VISTA product which draws SUS data into the same data pool and provides access to the combined data to both parties.
The project will continue for the foreseeable future.
|
||||
|
Background: Why is the new system/change in system/sharing of information/data processing required?
Incorporating the VISTA product will provide a richer, de-identified data set for CCGs and GPs that follows the care pathway from primary care to secondary care. Practices will also have the capacity to reidentify patients for the purposes of direct care.
|
||||
|
Overall Benefits:
Allowing a more comprehensive view of patient journeys, flagging of risks based on a more comprehensive data set.
Allowing parties to satisfy the statutory duty to share information provided by the Health and Social Care (Safety and Quality) Act 2015
“The relevant person must share information with;
(b)any other relevant health or adult social care commissioner or provider with whom the relevant person communicates about the individual
Where it would facilitate the care of the individual and the individual has not objected.
|
||||
|
Overall Constraints:
There is a need to ensure that transfers across organisational boundaries are lawful
There is a need to ensure that a Joint Controllership governance structure is in place
There is a need to ensure that patients have been provided with enough information and ample opportunity to object (including information about case finding and risk Strat as a profiling activity)
|
||||
|
Does the delivery of the project involve multiple organisations? If yes – please name them, and their project lead details:
CCGs
Practices
Prescribing Services Ltd
|
||||
|
Other Key Stakeholders and consultees:
Patients
|
||||
|
Does the PIA link to any procurement activity? If so, please detail at what stage of the process this PIA relates to and include relevant detail on the dates that the IG/IT assurances were obtained?
Procurement of Add On product (VISTA) from existing provider
|
||||
|
Does the project link to any other project management activity? If so give reference numbers of supporting project documents where known and include agreed project priority and timescales (e.g. CSU IT PMO, Annual planning cycle etc.)
Out of Scope for PSL to Comment
|
||||
|
Where the PIA relies upon documents submitted as part of PMO activities, please detail them here and attach them as part of your submission:
Out of Scope for PSL to Comment
|
||||
|
Has anything similar been undertaken before? If yes please detail:
The CCG are an existing user of the Eclipse Live product – introduction of the VISTA add on will result in an additional data set being drawn into the data pool.
|
||||
|
Information/Data – types/sources/collection/flows/legal basis/responsibility (you should be able to complete this part of the PIA from existing project plans/commissioning plans or other activity outcome document) |
|
1.1 What types of data/information will be used as part of this proposed activity? (Be specific e.g. Personal Confidential Identifiable Data (PCD), Corporate, Sensitive etc.)
The data will include extracted of identified personal data and special categories (sensitive) personal data
The data will be extracted, and a pseud no added within the “black box” environment CCGs will access de-identified data
GPs will have access to de-identified data with the ability to re-identify locally.
|
|
1.2 Why is this data/information being used?
CCGs will use to support risk stratification Practices will use the data for case finding purposes
|
|
1.3 How is the data/information being collected? (e.g. verbal, electronic, paper)
The data will be extracted from practice clinical systems either manually or via Apollo
SUS data will be provided by the CSU / CCG
|
|
1.4 Who is responsible for the data/information i.e. who is currently or will be the Data Controller/s? (You may need help from your Information Governance Lead to assist you with this part of the PIA).
The service requires CCGs and GPs to access and contribute to a single pool of data, used by more than one Controller for activities which have a common purpose and therefore the parties are Joint Controllers.
|
|
1.5 How is the data/information to be edited or deleted?
Beyond initial extraction, there will be regular periodic extractions from source. Where information has been amended at source, it is then reflected in the aggregated record in the next extraction.
|
|
1.6 How is the data/information to be quality checked?
PSL Data Quality Assurance doc
|
|
1.7 What business continuity or contingency plans are in place to protect the data/information?
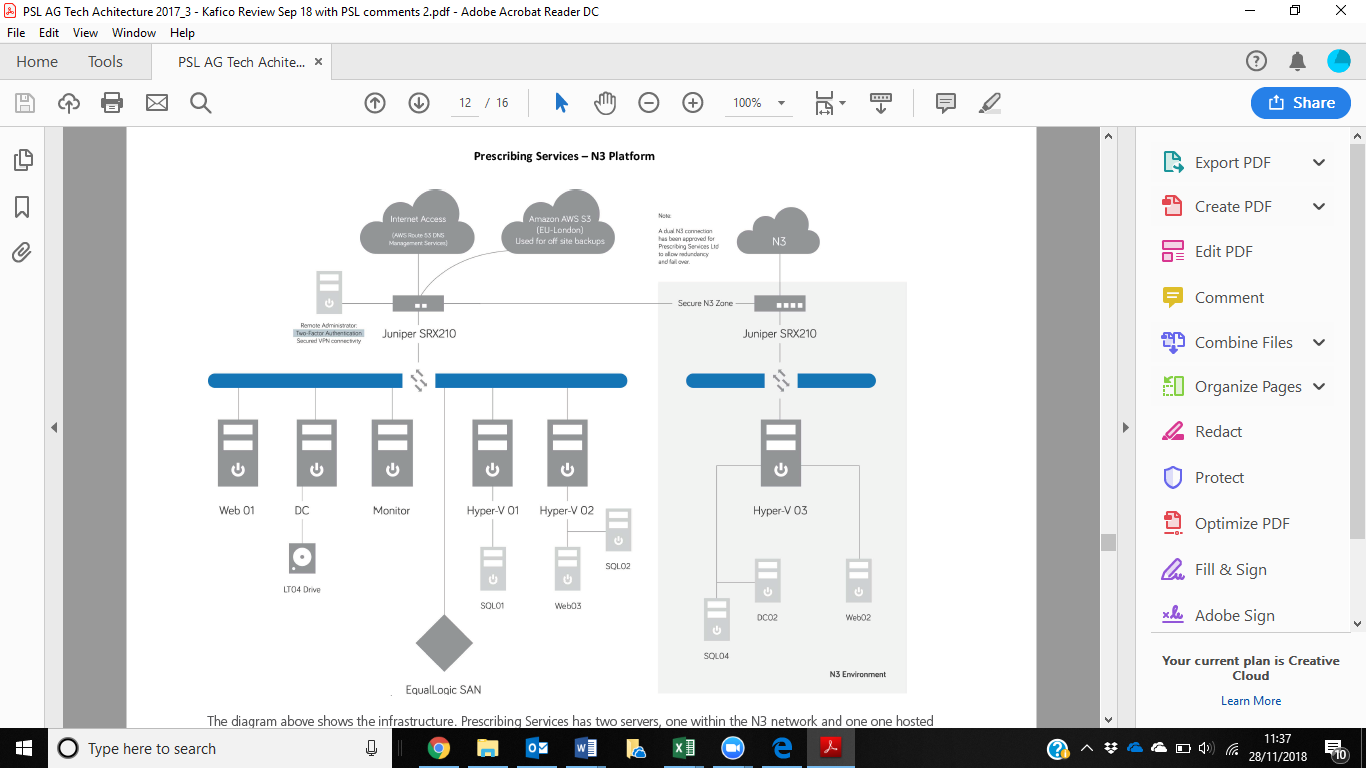
High Availability is implemented to reduce single points of failure. This is achieved at the database level using a virtualised environment hosted on a high availability SAN. Two virtual servers run SQL Server are hosted on different physical machines running on a high availability SAN. In case of VM failure standby takes over whiles original VM is rebuilt. We have purposely chosen a SAN with highly redundant components to allow failover in the case of failures. SQL Server's in built log shipping is used for this purpose which allows a mirror of the database to be created and kept current in a standby database. In the event of a failure the the secondary database is promoted to live and becomes the primary database to allow system functionality to continue. While this is a manual process early alerting systems allows a RTO of 10 minutes to be achieved. Following the resolution of the primary failure this database will become the secondary database with Log Shipping activated to ensure the database is current. The process to return to full redundancy requires the log shipping process to complete and will take 1.5 hours. High availability on the web layer is achieved using DNS management services and two web servers. Amazon Route 53 DNS management systems are set up to manage DNS routing and to monitor web servers. Health checks are in place that poll the primary web server (Web01) every 2 seconds. Should an outage be detected the DNS routing service automatically routes all traffic through to the secondary server (Web03) until the primary server is back on line at which point the routing is restored to the primary. This is an automatic process and allows a RTO of 10 minutes to be achieved. To reduce the risk of system outage only Advice and Guidance (Eclipse 24 and Eclipse Live) are hosted on an isolated instance of IIS web services on Web01. Other web-based services offered by Prescribing Services have been moved away from the primary web server. The N3 servers act as broker for extracts and for web access within the N3. Both services are not critical for the running of the application and as such do not utilise redundant technology. Both services require a very minimal configuration set and can be restored rapidly from a backup set using readily available architecture.
|
|
1.8 What training is planned (if required) to support this activity?
Out of Scope for PSL to Comment
|
|
1.9 Who are the Data Custodian/Information Asset Administrator and Information Asset Owner supporting the project/area/team this activity relates to?
Out of Scope for PSL to Comment
|
|
Information/Data – flows/legal basis/responsibility/sharing (you may need help from your Information Governance Lead and your Business Intelligence or Data Management support team to assist with this part of the PIA) |
|
2.1 For what purpose and under what Legal Basis are you proposing to use this Data/Information?
Out of Scope for PSL to Comment but presumed to be;
|
||||||||||||||||||||||||||||||||||||||||||
|
2.2 Are you proposing to link data sets in order to achieve the project/activity aims? If so, please detail the linkages.
Linkage of SUS+ and Primary Care Data
|
||||||||||||||||||||||||||||||||||||||||||
|
2.3 Are you proposing to share any data/information as a result of this activity? If so please detail the following What data/information is being shared? Why is this data/information being shared? Who are you sharing with? How will the data/information be shared?
Answered in previous sections
|
||||||||||||||||||||||||||||||||||||||||||
|
2.4 What are the Data Flows? (Please detail and/or attach a data flow diagram)
Primary Care Data Extracted from clinical systems SUS+ Provided by CCG / CSU Transmitted to Secure Gemini server (Black Box) Linked and validated using NHS No NHS No replaced with Eclipse No Transmitted to PSL Server Displayed at PSL portal interface
|
||||||||||||||||||||||||||||||||||||||||||
|
2.5 What information sharing protocols and operational agreements are or will be in place to support this sharing? As the parties are Joint Controllers, it is proposed that an Information Sharing Agreement is put in place that identifies the joint and several liabilities and responsibilities of each party and that the agreement is fully monitored through joint governance arrangements.
|
||||||||||||||||||||||||||||||||||||||||||
|
2.6 What reports will be generated from this data/information?
None – all viewing is online
|
||||||||||||||||||||||||||||||||||||||||||
|
2.7 Does this activity propose to use Data that may be subject to or require approval from NHS Digital?
No
|
||||||||||||||||||||||||||||||||||||||||||
|
2.8 If using NHS Digital data, is the new use covered by the purposes agreed under the existing Data Sharing Agreement?
Yes
|
||||||||||||||||||||||||||||||||||||||||||
|
Information/Data – Security (you may need help from your IT department or Information Security specialists to assist with this part of the PIA) |
||||||||||||||||||||||||||||||||||||||||||
|
3.1 Are you proposing to use a third party/data processor/system supplier as part of this project/activity?
Yes, Prescribing Services Ltd
|
||||||||||||||||||||||||||||||||||||||||||
|
3.2 How will the data/information be stored? The systems use a multi-tiered approach with a separate database layer, data access layer, business layer and presentation layer. Microsoft technologies are used throughout with best practices for development and maintenance employed by Microsoft Certified personnel. Both Eclipse 24 and Eclipse Live share the underlying database and application and as such share the same architecture.
|
||||||||||||||||||||||||||||||||||||||||||
|
3.3 Where will the data/information will be stored? (Include back-ups and copies)
Datacentres are hosted by The bunker secure hosting provides ultra-secure hosting solutions and is based in an ex-nuclear bunker in Kent. They have achieved ISO27001 and have completed their IG ToolKit. They provide services with the highest physical and logical security available. During 2015 Prescribing Services successfully completed IGSoC for the provision of an N3 connection directly into the Bunker. This allowed the creation of a hosting zone completely within the N3 network and only available to users within the N3.
|
||||||||||||||||||||||||||||||||||||||||||
|
3.4 How is the data/information accessed?
Server access is highly restricted both physically and logically. All access is restricted by role-based access only to those employees with a direct need to access the servers and is constantly monitored and audited.
Access over N3 to authorised parties is provided using secure Web applications and Web services limited to specific IP addresses. Enforcing 256bit AES encryption for all communication.
|
||||||||||||||||||||||||||||||||||||||||||
|
3.5 How will access be controlled and monitored depending on role?
Users are required to log on using a username and strong password combined with a second layer of authentication, which sends a single-use time-limited access code to the user’s personal mobile phone or email address. All data will be transmitted using SSL encryption and will not be stored on local machines. Access to information will be logged to allow full auditing to take place.
|
||||||||||||||||||||||||||||||||||||||||||
|
3.6 As part of this work is the use of Cloud technology being considered either by your own organisation or a 3rd party supplier?
Multi-tiered architecture. Partially on N3, partially on PSL hardware.
|
||||||||||||||||||||||||||||||||||||||||||
|
3.7 What security measures will be in place to protect the data/information (e.g. physical, electronic etc.)
RBAC / Access Controls IG Training for PSL Staff PSL DPIA PSL Audits Data Processing Contract (Article 28) Joint Information Sharing Agreement (Controller responsibility) Joint Governance Meetings (Controller responsibility) Joint Controller system audits Data encrypted in transit and at rest to 256 bit Pseudonymisation Back up measures in place Use of N3 Cross server anti-virus
|
||||||||||||||||||||||||||||||||||||||||||
|
3.8 Are you transferring any personal/sensitive data outside of the EEA?
No
|
||||||||||||||||||||||||||||||||||||||||||
|
3.9 Is a System Level Security Policy in place or required?
PSL Technical Architecture doc
|
||||||||||||||||||||||||||||||||||||||||||
|
3.10 Is the third party/data processor/system supplier registered with the Information Commissioner?
Z2536678 (PSL) Z8856975 (The Bunker)
|
||||||||||||||||||||||||||||||||||||||||||
|
3.11 What IG assurances can the third party/data processor/system supplier provide?
Internal DPIA drafted ISO 27001 system provider IGSoC and GPSoC IG Toolkit (Now Data Security Toolkit)
|
||||||||||||||||||||||||||||||||||||||||||
|
3.12 Does the contract with the third party/data processor/system supplier contain all the necessary IG clauses?
PSL Data Processing Contract has been reviewed against GDPR Article 28 and satisfies necessary clauses.
|
||||||||||||||||||||||||||||||||||||||||||
|
3.13 Is there or will there be a Data Processing agreement in place with the third party/data processor/system supplier?
PSL provide a compliant Data Processing Contract.
|
||||||||||||||||||||||||||||||||||||||||||
|
3.14 Who will be responsible for monitoring the contract/Data Processing Agreement with the third party/data processor/system supplier?
Practice Manager/Information Manager
|
||||||||||||||||||||||||||||||||||||||||||
|
3.15 Has the Data Processor been identified in any relevant DARs and DSA with NHS Digital (where appropriate – see 1.5 and 1.6 above)
N/A
|
||||||||||||||||||||||||||||||||||||||||||
|
Information/Data - consent/notification/retention (you may need help from your Information Governance lead to assist with this part of the PIA) |
||||||||||||||||||||||||||||||||||||||||||
|
4.1 Is consent from the data subject required?
No
|
||||||||||||||||||||||||||||||||||||||||||
|
4.2 What is the process for obtaining and recording consent/dissent from the Patient or Service User? (how, where, when, by whom) Include proposed consent form for review:
NA
|
||||||||||||||||||||||||||||||||||||||||||
|
4.3 If consent has not been obtained or is not required is there a legal basis to share data/information?
Out of Score for PSL as Processor but presumed to be..
|
||||||||||||||||||||||||||||||||||||||||||
|
4.4 What changes have been made or are proposed to Fair Processing Notices of the organisations involved (Privacy Notices)?
None
|
||||||||||||||||||||||||||||||||||||||||||
|
4.5 How can the Data Subject access any data/information relating to them as a result of this activity?
To be scoped as part of Joint Controller arrangements
|
||||||||||||||||||||||||||||||||||||||||||
|
4.6 How long is the data/information to be retained?
To be scoped as part of Joint Controller arrangements
|
||||||||||||||||||||||||||||||||||||||||||
|
4.7 How will the data/information be archived?
To be scoped as part of Joint Controller arrangements
|
||||||||||||||||||||||||||||||||||||||||||
|
4.8 What is the process for requesting the destruction of records?
Direct request made to PSL and Processor. Confirmed through Data Processing Contract.
|
||||||||||||||||||||||||||||||||||||||||||
|
4.9 What is the process for start-up and closing down this piece of work?
TBC by Controller customer
|
||||||||||||||||||||||||||||||||||||||||||
|
4.10 If the organisation/service ceases what will happen to the data/information?
Direct request made to PSL and Processor for return or secure destruction of data. Confirmed through Data Processing Contract.
|
||||||||||||||||||||||||||||||||||||||||||
|
Risks, issues and activities |
||||||||||||||||||||||||||||||||||||||||||
|
5.1 Are there any known risks or issues?
There may be a risk that the parties will not establish an effective joint controllership that includes demonstrable consideration of the joint and several liabilities of both parties. This information would also need to be made clear to data subjects.
Ensuring that fair processing materials are amended and visible to patients to support information rights.
|
||||||||||||||||||||||||||||||||||||||||||
|
5.2 Are there any known activities that will have a direct effect on this piece of work?
|
||||||||||||||||||||||||||||||||||||||||||
|
5.3 Any further comments to accompany this PIA that the panel should consider?
|
|
For IG Team completion only |
|
|
6.1 IG Manager (consulted or presenting) |
|
|
6.2 IG Manager comments/observations/specific issues |
|
|
Information Security Manager completion only |
|
|
7.1 Comments/observations/specific issues |
|
|
Business Intelligence/Data Manager completion only |
|
|
8.1 Comments/observations/specific issues |
|
|
Outcome of IG Panel |
|
|
Based on the information contained in this PIA along with any supporting documents, the outcome is as follows:
Reviewed with no further recommendations:
Reviewed with recommendations (list the recommendations):
Reviewed and recommended not to proceed at present: (provide brief summary of reason)
|
|
|
Signed on behalf of the Privacy Impact Assessment panel, NHS South, Central and West Commissioning Support Unit subject to any recommendations detailed above:
Name: …………………………………………………………….
Job Title: ………………………………………………………….
Signature: ……………………………………………………….. Date: ………………………………….
Signed and approved on behalf of ………………………………………………………………………….... (Caldicott Guardian or Senior Information Risk Owner to sign)
Name: …………………………………………………………….
Job Title: ………………………………………………………….
Signature: ……………………………………………………….. Date: ………………………………….
|
|
|
Please note: Where further evidence has been requested by SCW CSU IG PIA panel, in cases where the original recommendation has been assessed as either ‘Reviewed with recommendations’ (and a further review is needed) or ‘Reviewed and recommended not to proceed at present’ this must be received by the PIA Panel within a maximum timeframe of three months from the date of original submission. If the required evidence is not received in this timeframe the PIA will be closed. It is the responsibility of the Project/Activity Lead to notify the appropriate Information Asset Owner/Data Custodian/Information Asset Administrator for inclusion on the Information Asset Register and Data Flow Mapping. |
|
Appendix A – Prescribing Services – N3 Platform
Page
2 PRIVACY ACT COMPLAINT FORM DATE 1 YOUR
30TH ANNIVERSARY OF THE OECD PRIVACY GUIDELINES REMARKS BY
8S PRIVACY SECURITY MINIMUM NECESSARY LIMITED DATA SET AND
Tags: activities that, known activities, activities, involve, assessment, projects, privacy, impact, template
- PRESS RELEASE MARCH 22 2010 LEICA MICROSYSTEMS PRESENTS INNOVATIVE
- COMPLEJOS I 1 RESOLVER EN EL CONJUNTO DE LOS
- PORTUGÁLIAEGY IGAZI ÉKSZERDOBOZ FATIMA A 100 ÉVES CENTENÁRIUM FÉNYÉBEN
- COMBINED ANNUAL FACTBOOK SURVEY FOR ASSOCIATION OF INDIANA COUNTIES
- W ELCOME TO WORSHIP ‘PALM SUNDAY THE TRIUMPHAL
- Nº 79 BOLETÍN DE LA ASOCIACIÓN DE VECINOS BAJO
- LA DGT CREA UNA NUEVA INSTRUCCIÓN PARA MEJORAR LA
- TRIBUNALE DI ATTO DI CITAZIONE EX ART 784
- DECKVERTRAG VERSAND VON GEFRIERSAMEN H & D SCHULZ QUARTER
- WWWMONOGRAFIASCOM MANUAL DE POWER POINT MENÚ ARCHIVO NUEVO ESTE
- QUESTI GLI INTERVENTI PIÙ IMPORTANTI PREVISTI NELLE SINGOLE PROVINCE
- LA NOCIÓN DE SISTEMA TERRITORIAL DE INNOVACIÓN APLICADA A
- REPORT SUMMARY APPRENTICESHIPS FOR YOUNG PEOPLE A GOOD
- SCHOOL RENTAL CONTACTS SCHOOL CONTACT TELEPHONE COS COB ELEMENTARY
- (12041024) 2 ELEKTRONIESE BEHEER EN DIGITALE ELEKTRONIKA NKR VLAK
- ORDENANZA MUNICIPAL DE GESTIÓN RECAUDACIÓN E INSPECCIÓN I PRINCIPIOS
- STI CONFERENCE 2018 · LEIDEN TEMPLATE FOR SUBMISSION OF
- SENZORI U AUTO INDUSTRIJI I SISTEMI ZA DIJAGNOSTIKU WWWMATURSKIORG
- F RANCISCO ALBERTO PÉREZ PIÑÓN MAESTRO EN EDUCACIÓN SUPERIOR
- SMIS RŪPINTIS SAVO SVEIKATA GALIME IŠMOKTI NEGALUOTI PRADEDA VIS
- LINEAR FUNCTIONS OF RANDOM VARIABLES IT OFTEN HAPPENS THAT
- 2 OBERLANDESGERICHT BESTÄTIGT FREISPRÜCHE ZWEIER FEUERWEHRLEUTE VOM
- WETTBEWERB BESTE MARKETINGKAMPAGNE ZU ENERGIEEFFIZIENTEN TOPTENPRODUKTEN EINLADUNG 6 OKTOBER
- CORSO DI LAUREA IN OSTETRICIA I ANNO – II
- OGGETTO RICHIESTA DI COMPENSAZIONE TERRITORIALE AI SENSI DELLART 5
- APPENDICE 1 CENNI SULLE RETI DI COMPUTER E SERVIZI
- TC498 PÁGINA 6 S TC498 ORIGINAL INGLÉS FECHA 21
- TOSHIBA SATELLITE 1200 HOW TO TAKE APART LAPTOP STEP
- ZWIĄZEK STOWARZYSZEŃ SPORTOWYCH „SPRAWNI – RAZEM” W WARSZAWIE ORAZ
- OEA XXXIV CURSO DE DERECHO INTERNACIONAL ASPECTOS JURÍDICOS DEL
XXIX TORNEO DE AJEDREZ “VILLA DE ALMONTE” 2016
WORKING GROUPS REFERENCE DOCUMENTS BREF WORKING
KAYSERİ SANAYİ ODASI BAŞKANLIĞINA ……202… ODANIZIN ………… SICIL NOLU
LIETUVOS INSULTO ASOCIACIJOS KONFERENCIJA – 2019 IR VISUOTINIS NARIŲ
 BOLETIN Nº 16 REUNION 13052014 CONSEJEROS PRESENTES FERNANDO MARTONI
BOLETIN Nº 16 REUNION 13052014 CONSEJEROS PRESENTES FERNANDO MARTONICEIP SANTIAGO APÓSTOL MIRANDA CARTAGENA PROYECTO CURRICULAR DE PRIMARIA
 NEW SCHEDULER UTILITIES ORACLE 10G PROVIDES A NEW
NEW SCHEDULER UTILITIES ORACLE 10G PROVIDES A NEWMIÉRCOLES 21 DE AGOSTO DE 2013 DIARIO OFICIAL (PRIMERA
EPOCHEN SYNOPTISCH VON DER ROMANTIK ZUR MODERNE (PETER DEUTSCHMANN
MODÈLE DE LETTRE POUR LA PRÉSENTATION DU DÉLÉGUÉ AUX
MIGRAINE PATHOPHYSIOLOGY — MIGRAINE IS THOUGHT TO HAVE A
SVEUČILIŠNA KLINIČKA BOLNICA M O S T A R
 NAS901056 SECTION JC PART III LIST OF DOCUMENTS
NAS901056 SECTION JC PART III LIST OF DOCUMENTSUMOWA KONSORCJUM ZAWARTA W DNIU …………R POMIĘDZY STRONAMI
MUNICIPIUL SATU MARE SERVICIU EVIDENŢĂ PATRIMONIU CONCESIONARI NR 224219012016
NORTHERN SYDNEY EDUCATION & CONFERENCE CENTRE (NSECC) ROOM
INSTRUCTIONAL QUALITY COMMISSION IQC001 (032012) STATE OF
 IF YOU ARE LIKE MANY PEOPLE THESE DAYS YOU
IF YOU ARE LIKE MANY PEOPLE THESE DAYS YOUPROJET DE RECHERCHE FINANCÉ PAR L’ACADÉMIE HASSAN II DES
LEGISLACIÓN SALUD LEY 23660 LEY DE OBRAS SOCIALES BENEFICIARIOS